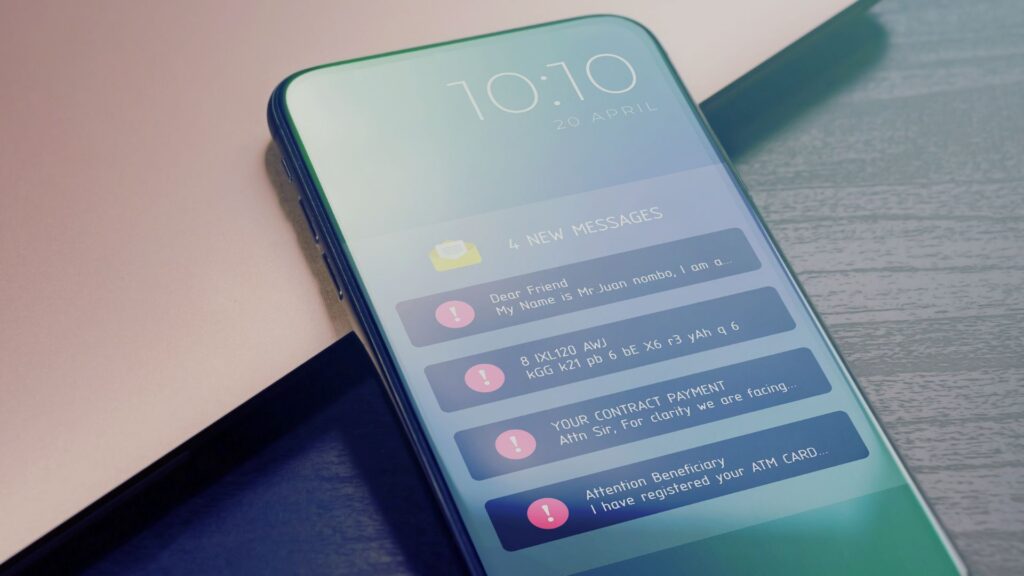
What Is Whaling? Go Big Or Go… Whale!
What if the cyberattack wasn’t targeted at just anyone, but instead aims straight for the C-suite or company’s leaders? It’s not just a phish. It’s not a simple scam. This is “whaling”. It’s a big game, the stakes are high, the attacks are sophisticated, and the damage can be devastating. Let’s get started. What is […]
What Is Whaling? Go Big Or Go… Whale! Read More »